 When it comes to data breaches, nobody bears the brunt like online businesses. While 46% of Americans have fallen victim to credit card fraud within the past five years, fraudulent purchases can be reported to the credit card company which will usually initiate a chargeback, reimbursing the customer his or her money. In the end, it’s the merchant who must pay for stolen information, whether that information was stolen from them or not.
When it comes to data breaches, nobody bears the brunt like online businesses. While 46% of Americans have fallen victim to credit card fraud within the past five years, fraudulent purchases can be reported to the credit card company which will usually initiate a chargeback, reimbursing the customer his or her money. In the end, it’s the merchant who must pay for stolen information, whether that information was stolen from them or not.
But who is stealing these credit card numbers, and where do fraudulent charges come from? More importantly, how do they carry on doing it without getting caught? To answer this question, we must venture into the farthest frontier of organized cybercrime today, a part of the Internet which lies hidden from plain sight: the notorious Dark Web.
Our journey begins with data breaches, and the art of stealing personal information.
How Credit Cards are Compromised
Credit card theft is an old and sophisticated art. Before the advent of chip cards which use integrated circuits to offer cardholders an extra layer of protection, ATM machines, gas pumps and other points-of-sale could be outfitted with false exteriors to skim information from a credit card’s magnetic strip.
While more sophisticated versions of the skimming attack continue – especially in big cities and tourist destinations – the most prevalent form of credit card theft today involves hacking the records stored on a merchant’s server or compromising their websites to collect payment information entered by the customer.
Last year, at least 7,339 online stores using the Magento eCommerce platform were compromised by the Magento Core malware, which used a form of “digital skimming” to swipe credit card information as it was entered by customers and transmit it to cybercriminals.
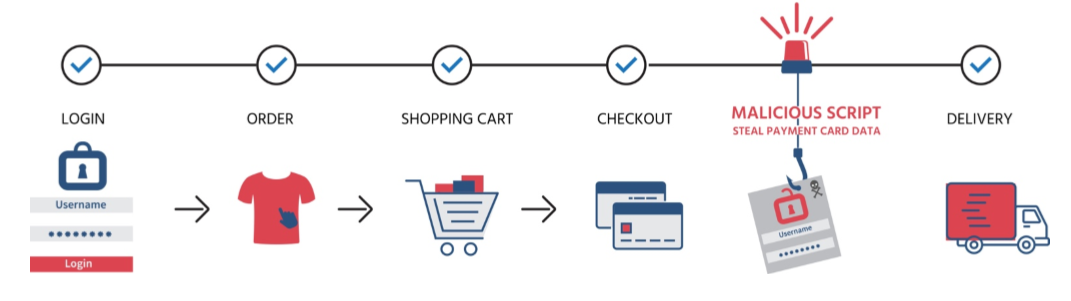
Magento Core is similar to Magecart and Magecart-style malware which have targeted eCommerce sites since 2014. But these account for only a portion of credit card theft: sometimes hackers will spend months or even years penetrating the innermost core of a company’s digital records, as Marriott Hotels learned the hard way last year, when up to 500 million guest records were compromised by a breach four years in the making.
But just how many online businesses are at risk of being targeted in this way? According to the research, almost all of them: 80-90% of all login-attempts on retail sites can be traced to “credential stuffing attacks,” which hackers use to take over customer accounts. If you’ve never understood the point of login captchas, now you do.
The Dark Web Explained
During a data breach or Magecart style attack, millions of records can be stolen. But what do attackers do with all this data? Typically, they are sold on darknet markets, or used to purchase goods which are sold on darknet markets.
But what are darknet markets, and how do they work? A lot of misinformation abounds: the terms “Dark Web,” “Deep Web” and “Darknet” are used interchangeably, when they are not the same things. Here’s a simple rundown:
- A darknet is part of the deep web. There may be many darknets, but the most popular is The Onion Network which uses the .onion top-level domain (TLD).
- The deep web is a non-indexed portion of the World Wide Web, mostly dedicated to traffic unreadable by humans (iOT, streaming services) and private services (email, personal login portals, etc.)
- The World Wide Web is an information space stored on the Internet, and accessible through the Hyptertext Transfer Protocol (HTTP). Websites are interconnected (hyperlinked) documents that can be indexed and found via search engines,
- The Internet is a series of computer networks that are connected to each other through the Internet Protocol Suite (TCP/IP). Not everything on the Internet is a website, or accessible through the Web; but everything on the Web is part of the Internet.
The following graphic shows the relationship between these different terms and technologies:

It’s important to note that – in spite of its reputation – not everything related to the Deep Web or Darknet is illegal, fraudulent, or bad. The Deep Web is nothing more than a necessary shadow side of the technology which powers the Internet, while Darknets can be used for many purposes, some of them mundane.
Due to the anonymity they provide users, however, Darknets are inevitably the hubs of cybercriminal activity. To understand what that looks like, we’ll take a closer look at TOR, the best known Darknet in public consciousness.
The Onion Router (TOR)
TOR began as a Navy project to obscure the origin of Internet traffic. Although intended to protect military targets, it was eventually released as an open-source project for anyone to use, and that is how it became what it is today.
TOR disguises the identity and location of its users in two ways:
- Traffic is protected under several layers of encryption (hence ‘onion’), making it impossible to decipher before it reaches an exit node
- TOR traffic is bounced among several different “nodes” or relays before arriving at its destination. While this makes the network notoriously slow, it also makes identifying the source of traffic extremely difficult
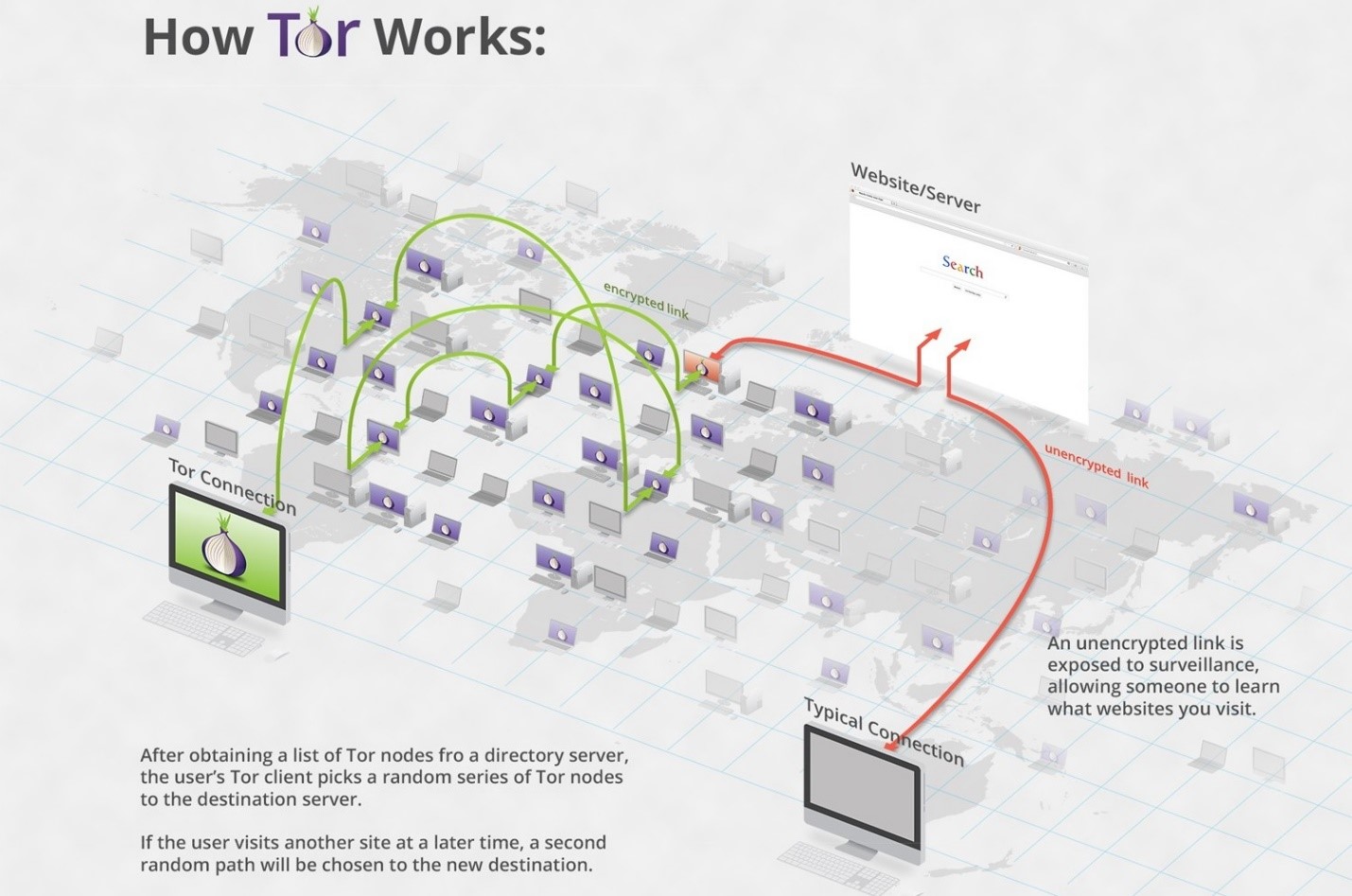
The TOR network can only be accessed through variations of the TOR browser, and while it can connect to websites on the indexed Web, it is also the only way to access onion domains (.onion).
Darknet Markets
Several years ago, the FBI managed to shut down a TOR marketplace known as The Silk Road. The story of this operation is thrilling, but also an exception to the rule: it is almost impossible for government agencies to shutdown Darknet markets in most cases, and many continue to abound.
Stories regale of the things that can be bought through TOR, most of them illegal. Some of these stories are exaggerated (there are probably no authentic kill-for-hire sites), while some are absolutely true. On TOR, users can purchase:
- Illegal drugs of almost every stripe (some markets draw the line in certain places; for instance, Dream Market famously refuses to accept Fentanyl listings)
- Firearms, stolen or otherwise
- Stolen merchandise at marked-down rates
- Stolen financial information including credit card numbers, PayPal accounts, and bank credentials
What follows is a screenshot from the Agora marketplace, with access information redacted:
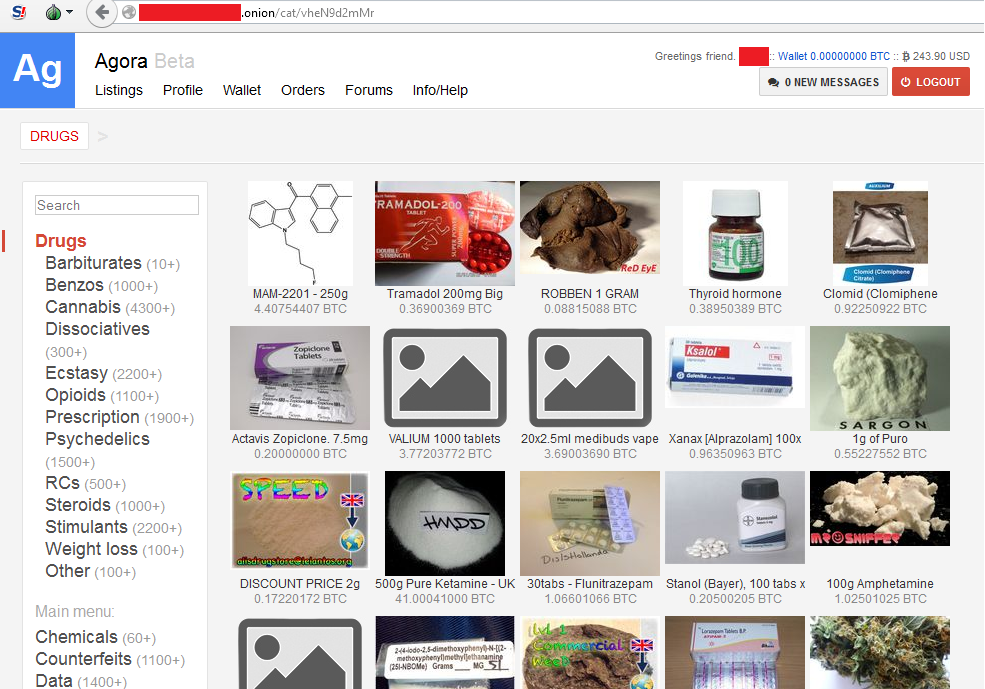
To avoid traceable purchases, vendors almost exclusively accept cryptocurrency like Bitcoin through escrow, enabling customers to retrieve their money in case their purchases are not received for any reason.
Darknet markets are surprisingly well-regulated, with complex systems of vendor verification, user reviews and quality control. This ensures that only the most reliable cybercriminals achieve success on the Dark Web and makes credit card fraud a well-organized operation at every level.
Profiting from Credit Cards
Offloading ten million credit card numbers isn’t easy, and cybercriminals have come up with various ways to do it over the year. There are three common methods:
- Selling directly
In some cases, hackers will sell stolen credit card numbers directly to buyers. While this is how most people imagine credit card fraud works, it’s considered risky for two reasons:
- Security groups monitor Darknet markets and may alert the cardholder if their information ever makes an appearance. Simply listing a stolen credit card can therefore get the account closed, making it worthless to both the buyer and seller.
- Buyers are wary of using stolen credit card numbers as the purchases can easily be traced, putting a target on their heads should law enforcement get involved.
Nevertheless, this form of fraud is practiced in some markets, as shown in the screenshot below:
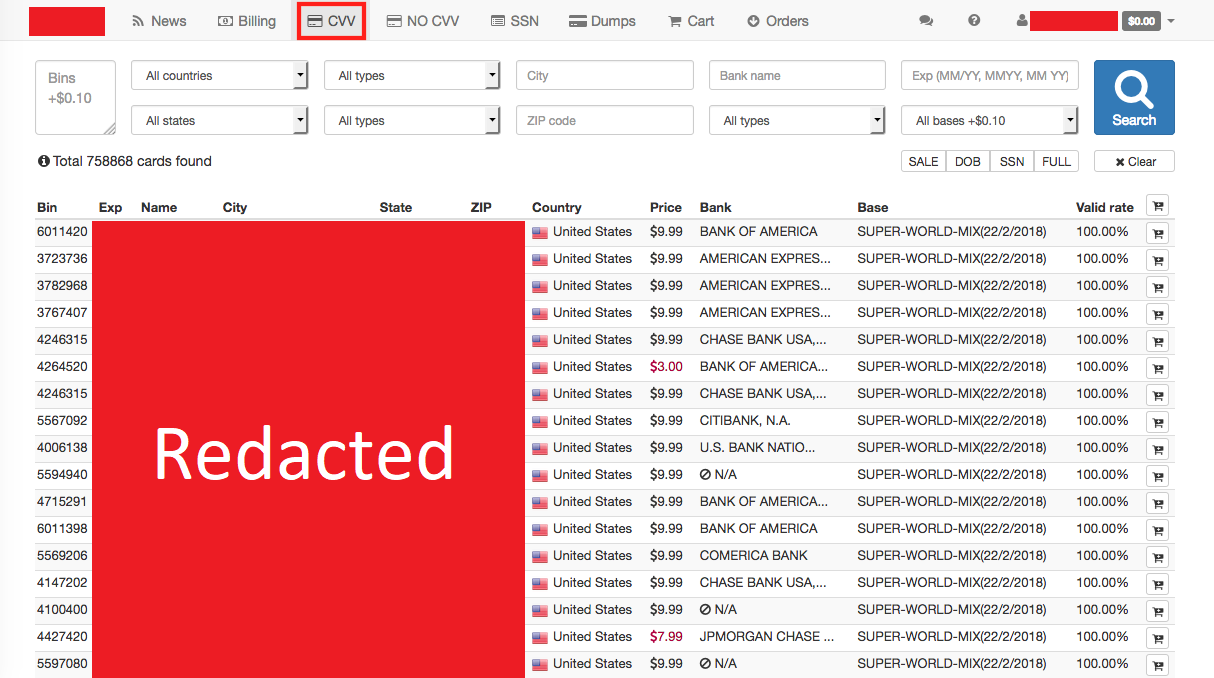
More typically, the perpetrators behind mass data breaches will sell credit card numbers in bulk, and the second-hand buyers will find more creative uses for them. This brings us to #2:
- Triangulation Fraud
In a triangulation scheme, cybercriminals sell merchandise without inventory on legitimate marketplaces like eBay, typically at competitively low rates. When a buyer purchases the item, the criminals buy and ship it in their name from a legitimate online business.
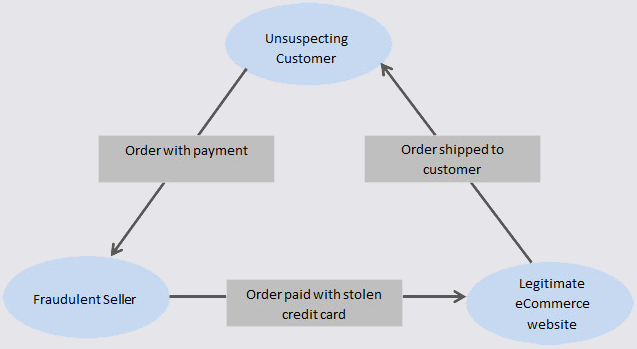
This approach has two advantages:
- It allows the seller to build a seemingly legitimate business, providing a plausible explanation for their ill-gotten gains
- If the fraud is investigated, suspicion will fall on the unsuspecting buyer, since the purchase can be traced to their name and address
Unfortunately, triangulation also creates three victims: the card owner whose money is stolen, the buyer who may be identified as the culprit, and the legitimate business owner who may end up fronting a chargeback if the fraud is reported.
- Selling Prepaid Cards
In many cases, cybercriminals will simply purchase prepaid cards with stolen numbers and sell them to buyers on Darknet markets. Cybercriminals can acquire prepaid cards without fear of detection, buyers can use them without being traced, and – in the case of chargebacks – the prepaid card will not be de-activated.
Protecting Your Business
As the owner of an online business, being targeted by cybercriminals or caught up in a triangulation scheme isn’t a matter of “if” but “when”. While there is no way to be 100% safe, there are ways to protect yourself.
Firstly, we cannot overemphasize the importance of website security. Cybercriminals use scanning software to find websites with easy vulnerabilities and target them first. Shield your site from common attack vectors by:
- Investing in cybersecurity to identify potential XSS attacks, SQL flaws, vulnerable third-party code and more
- Do not allow file uploads to your website unless absolutely necessary
- Regularly updating the software and plugins on your site; new releases usually include patches for security flaws
Second, to avoid triangulation fraud, consider investing in a fraud detection system which can detect and block suspicious activity such as repeat transactions from a single point-of-sale.
When it comes to fraud, the majority of online businesses do not suffer from too much vigilance. Being proactive rather than reactive could save you from disaster.
Conveyance Marketing Group is a team of bright, innovative and talented veteran marketers dedicated to big ideas, fresh insights and measurable results. We pride ourselves on taking challenging marketing issues and turning them into opportunities for our clients, on pointing brands in the right direction, and on getting our customers noticed both online and off. From branding to websites to digital marketing, and public relations, we handle all your marketing communication needs! Web Design and Development | Brand Strategy | Inbound Marketing | Social Media | SEO | PR
